Vulnerability scanning can be done weekly or monthly if properly automated.
Beyond security vulnerability scanner.
We always know what is going on around us previously i have dealt with many many different scanning vendors in my 15 years in it security.
And the reason behind this is simple.
Accuracy flexibility and simplicity vulnerability assessment and management solutions that deliver solid security improvements based on testing accuracy flexibility and low maintenance.
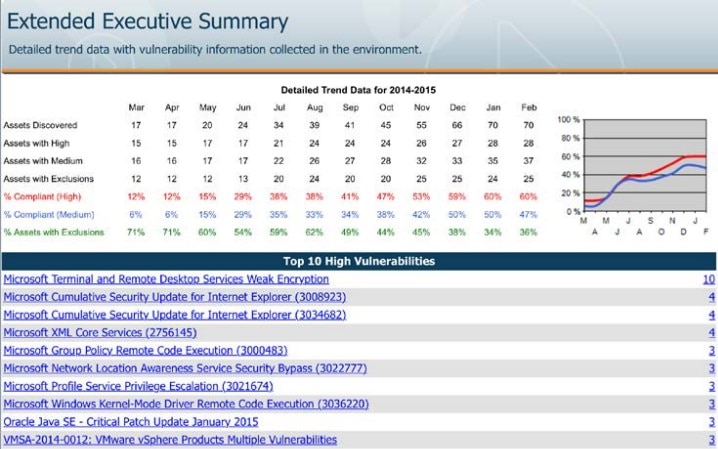
Regular vulnerability assessments scans are like having sonar on our own network.
Deltavineworld uk was tested on.
Beyond security brings a serious team to the process and it seems that its approach is solid and novel.
Sites that are regularly security tested by wssa can eliminate the vulnerabilities that allow hackers in and keep this from happening.
Your vulnerability scanner needs to complement support and simplify your work on meeting compliance standards and to do this with actual and measurable improvement in network security.
Beyond security is a global leader in automated vulnerability assessment and compliance solutions enabling businesses and governments to accurately assess and manage security weaknesses in their networks applications industrial systems and networked software at a fraction of the cost of human based penetration testing.
Besecure from beyond security is the first solution i could power up configure and start doing useful scans.
For every 0 day there are.
The 5 human elements of cybersecurity every cso should review.
We also like that the product leverages the team s core competence in maintaining the securiteam knowledge bank.
Top 10 tips to improve web application security.
Vulnerability free what is this.
Accuracy anything less than pinpoint accuracy wastes resources.
Learn about beyond security upcoming events and get the latest cybersecurity news blogs and tips.
We develop automated comprehensive and easy to use security testing solutions that help companies government and the military secure their networks websites and software products.
Inaccurate testing or incomplete reporting can turn your vam.
Closing the door on network attacks using security scanning tools vulnerability assessment the security scanning tool of choice unless your network is very noteworthy and very secure it is going to be attacked with a known exploit not an unknown one aka.
Formerly retina network security scanner reduce risk with cross platform vulnerability assessment and remediation including built in configuration compliance patch management and compliance reporting.